CTF Writeup | USB100
This is a writeup for the USB100 CTF challenge from Blackhat CTF.
I participated in this competition with the bER4bb1t$ CTF team and had a lot of fun with the challenges.
Altough this was an easy challenge it took me quite some time to solve it.
Attached to the challenge was a PCAP file which showed some USB traffic when opening it in Wireshark.
My first thought was that this traffic was from a USB keyboard due to a past CTF challenge. But it turns out my hunch was wrong and it there were some file transfers happening instead.
Quick sidenote:
I solved this challenge a very complicated way and went an extra mile I didn’t have to. If you want to read the simpler version please checkout the very well written writeup from InFeRnOo which you can find on his blog.
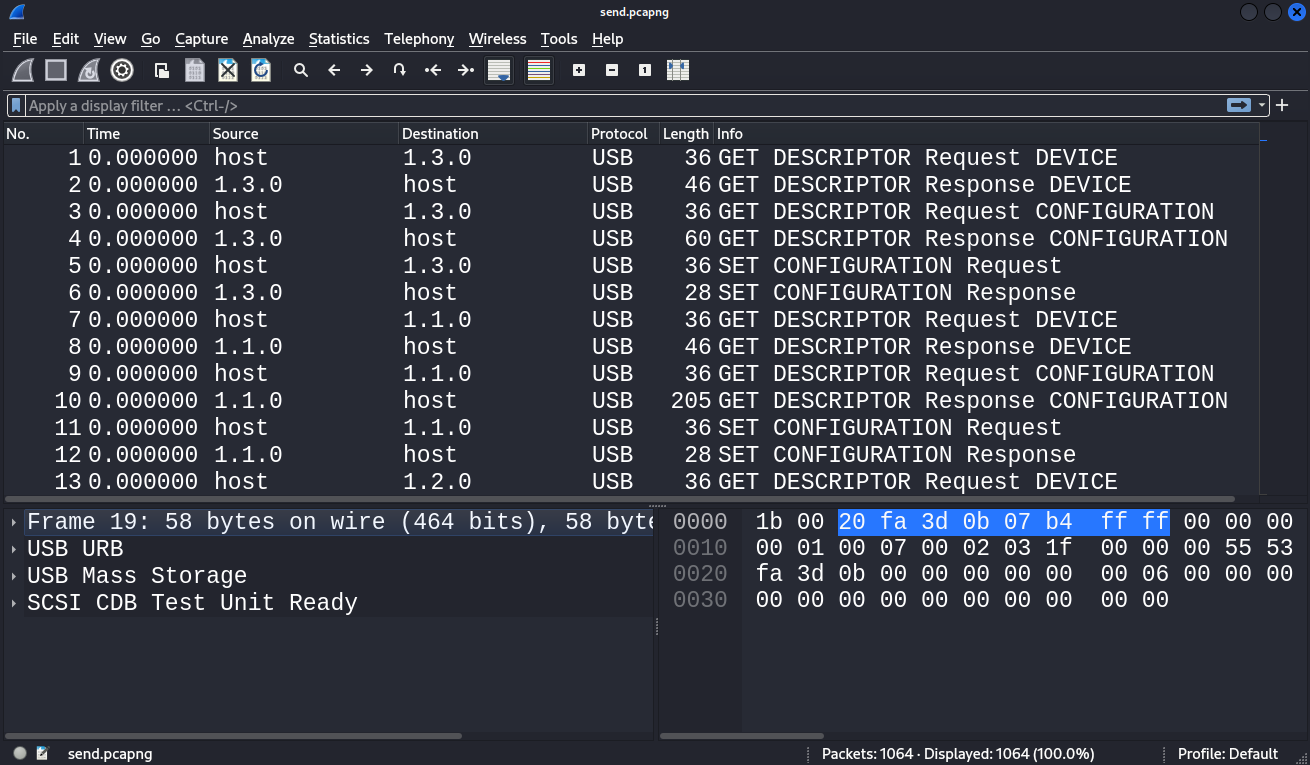
I noticed that some interesting data was transferred in packets from the USB protocol described as “URB_BULK out”.
After looking at the wireshark documentation we can use the filter usb.capdata to filter out these packets. To be more precise the interesting data is in the Leftover Capture Data field which we can add as a column by right clicking it.
To work with this data better I used tshark to filter the data in the terminal.
$ tshark -r send.pcapng -Y 'usb.capdata' -T text
85 15.483881 host → 1.7.2 USB 4123 52435...7c38000… URB_BULK out
91 15.485612 host → 1.7.2 USB 4123 52435...8c58000… URB_BULK out
97 15.487361 host → 1.7.2 USB 4123 46494...0000000… URB_BULK out
103 15.489464 host → 1.7.2 USB 16411 ffd...607070609… URB_BULK out
109 15.493185 host → 1.7.2 USB 4123 5243...cec58000… URB_BULK out
115 15.499419 host → 1.7.2 USB 4123 5243...f1c58000… URB_BULK out
121 15.501246 host → 1.7.2 USB 4123 5243...cec78000… URB_BULK out
127 15.503022 host → 1.7.2 USB 4123 4649...00000000… URB_BULK out
133 15.505004 host → 1.7.2 USB 65563 ffd...405050406… URB_BULK out
139 15.513381 host → 1.7.2 USB 4123 5243...e4c78000… URB_BULK out
Now we can extract the packets into one single hex file:
$ tshark -r send.pcapng -Y 'usb.capdata' -T fields -e usb.capdata > raw-r: Packet file to read data from
-Y: Display filter
-T: Set the output format to ‘fields’
-e: Adds field to list of fields to be extracted
To really work with this data I converted it to one binary file using xxd
$ xxd -r -p raw output.bin-r: reversed the hexdump into binary
-p: plain hexdump style
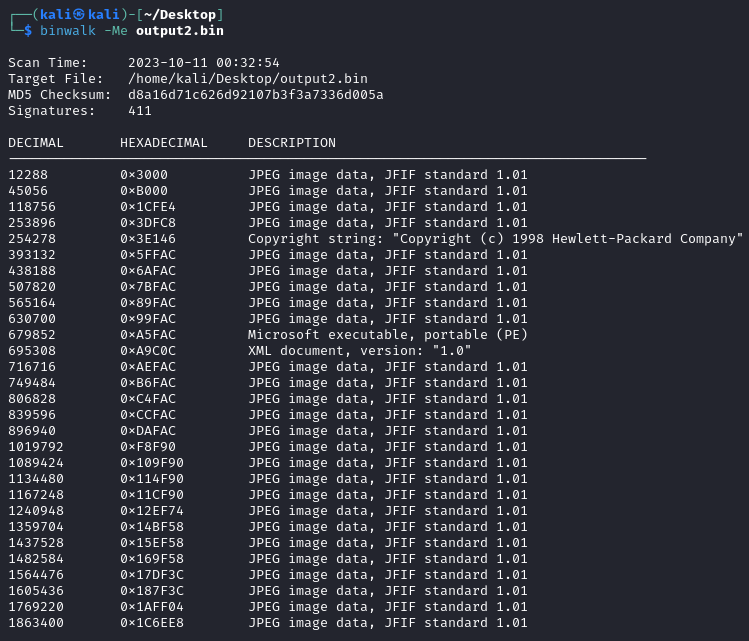
Now we can look what data we extracted using binwalk:
The ‘Microsoft executable’ is looking a little suspicious so lets extract the files and take a closer look:
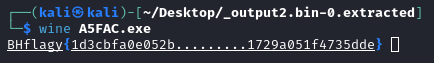
$ binwalk --dd='.*' Now we just need to rename the executable to a .exe and execute it either on windows or usig wine.
Thank you for reading.